Ever wondered how devices on a local network find each other? That’s where the ARP Protocol comes in. It’s a small but mighty part of networking that ensures your data knows where to go. Let’s break it down in a way that actually makes sense!
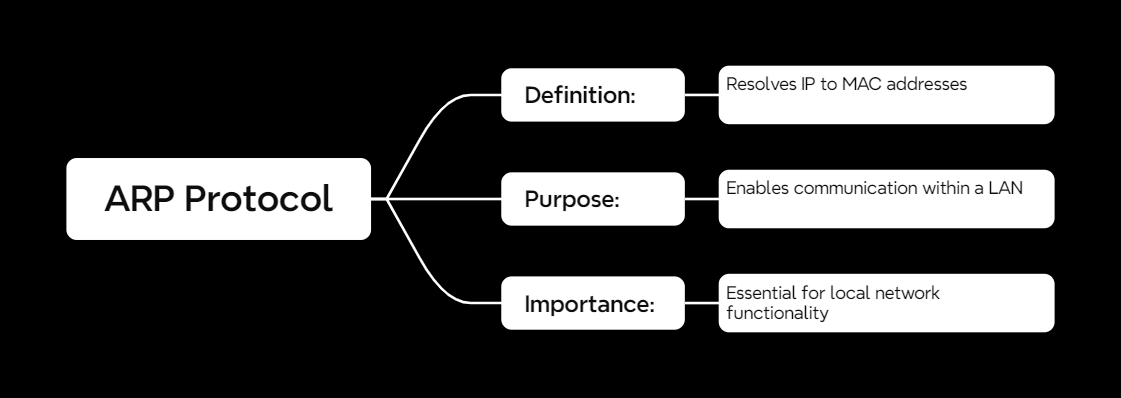
What Is ARP?
ARP stands for Address Resolution Protocol. Its main job? Translating an IP address (the digital “name” of a device) into a MAC address (its physical “phone number”). Without ARP, devices on a local network would be like strangers trying to call each other without knowing anyone’s number.
How Does ARP Work?
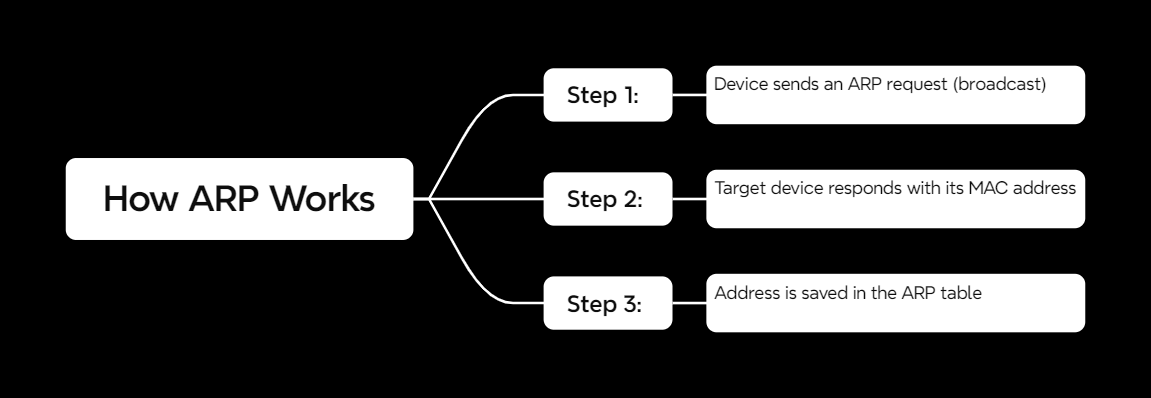
Here’s how the magic happens:
- Broadcasting a Request
- When Device A wants to talk to Device B, it sends an ARP request:
“Hey, who has this IP address? Send me your MAC!”
- When Device A wants to talk to Device B, it sends an ARP request:
- Getting a Reply
- Device B sees the request and responds with its MAC address:
“Yo, that’s me! Here’s my MAC!”
- Device B sees the request and responds with its MAC address:
- Storing the Info
- Device A saves this info in its ARP table so it doesn’t have to ask again.
Real-Life Example
Think of it like sending a letter. You know the recipient’s name (IP address) but need their street address (MAC address). ARP is your friendly post office, finding that address for you.
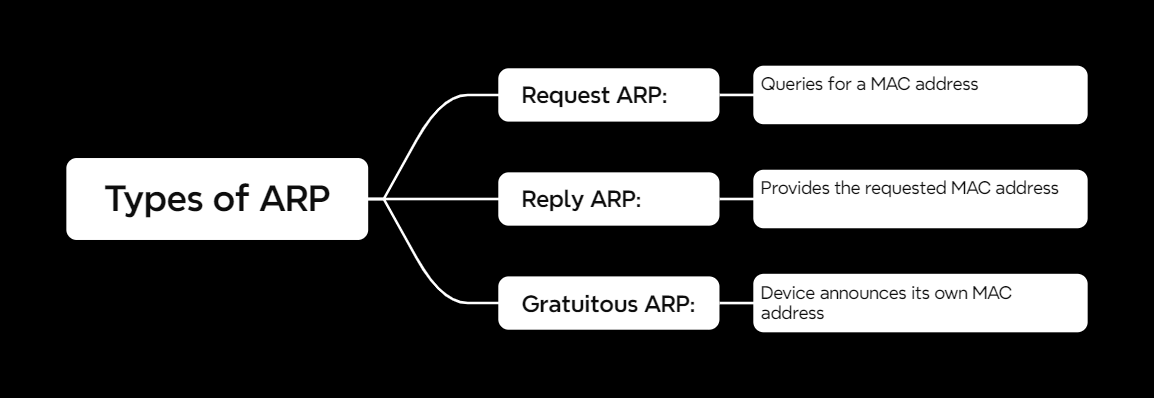
Types of ARP
ARP isn’t a one-size-fits-all deal. Here are its main types:
1. Request ARP
- This is your typical “Who has this IP?” query.
2. Reply ARP
- The response to a request, providing the MAC address.
3. Gratuitous ARP
- A device announces its own IP-MAC mapping, like saying, “Hey everyone, here’s my info!”
ARP Table: Your Device’s Cheat Sheet
Every device keeps a little “cheat sheet” called the ARP table, mapping IP addresses to MAC addresses.
How to View It:
- Windows: Open Command Prompt and type
arp -a - Linux/Mac: Open Terminal and type
arp -a
You’ll see something like this:
1
2
192.168.1.1 00:11:22:33:44:55 dynamic
192.168.1.100 66:77:88:99:AA:BB dynamic
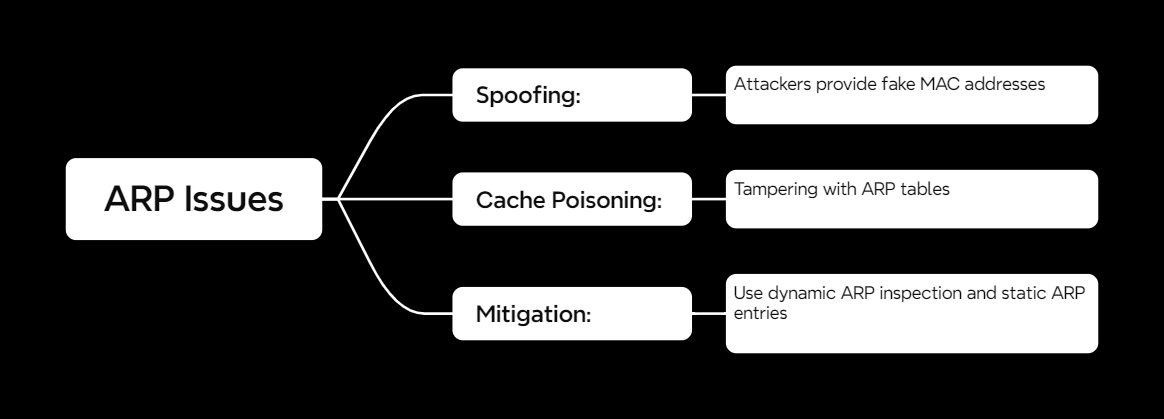
ARP’s Vulnerabilities
Unfortunately, ARP isn’t perfect. Here are its main weaknesses:
1. ARP Spoofing
- An attacker pretends to be another device by sending fake ARP replies, tricking devices into sending data to the wrong place.
2. ARP Cache Poisoning
- Tampering with ARP tables to misroute data or eavesdrop on communications.
Mitigation Strategies
- Dynamic ARP Inspection: Monitors ARP traffic for abnormalities.
- Static ARP Entries: Manually map IP-MAC pairs for critical devices.
Why ARP Matters
Without ARP, local networks wouldn’t function. It’s the glue that holds everything together, ensuring devices can communicate seamlessly. Whether you’re gaming, streaming, or working, ARP is working behind the scenes to make it happen.