Ever wonder how your computer knows if a website is down or if a router is too slow? Meet ICMP, the Internet Control Message Protocol. It doesn’t send actual data like TCP or UDP—it just helps devices talk about network issues. Think of it as the network’s error reporter and troubleshooter.
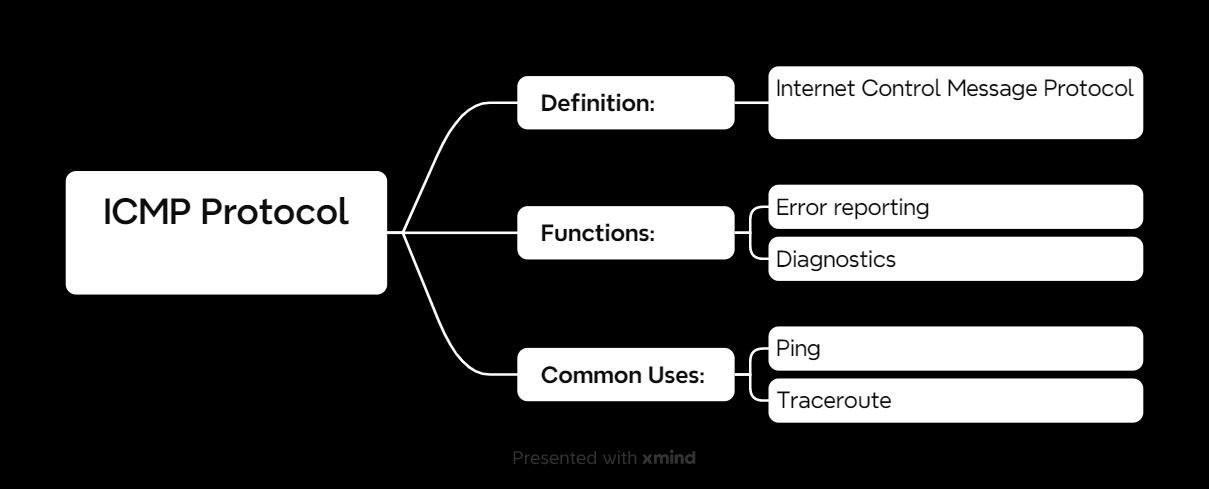
What Is ICMP?
ICMP (Internet Control Message Protocol) is a network protocol used for:
✅ Error reporting: Helps devices know when data can’t be delivered.
✅ Diagnostics: Used for tools like Ping and Traceroute to check network connectivity.
Unlike TCP or UDP, ICMP isn’t used to transfer data. Instead, it works behind the scenes, sending control messages to keep the network running smoothly.
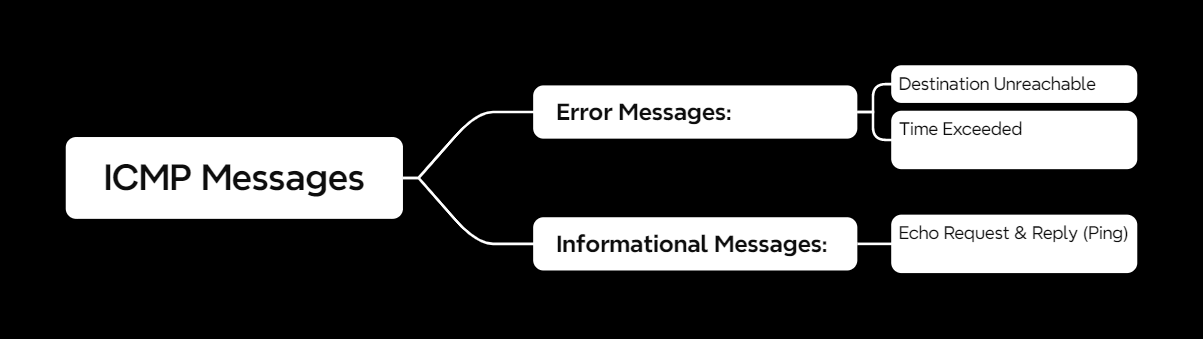
ICMP Message Types
ICMP messages come in two main types:
1️⃣ Error Messages
These let devices know when something goes wrong:
- Destination Unreachable: “I can’t find that IP!”
- Time Exceeded: “This packet took too long to arrive!”
- Redirect: “Hey, use a better route for this!”
2️⃣ Informational Messages
Used for diagnostics:
- Echo Request & Echo Reply: Also known as Ping, this checks if a device is online.
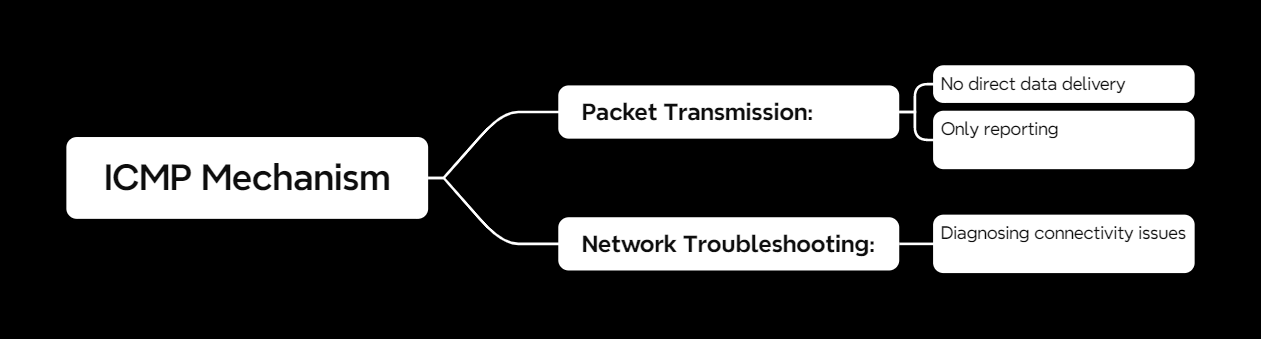
How ICMP Works
When you ping a server, here’s what happens:
1️⃣ Your device sends an ICMP Echo Request to the target.
2️⃣ If the server is up, it responds with an Echo Reply.
3️⃣ If something’s wrong, your device might get an ICMP error message instead.
ICMP is also used in Traceroute, which helps find the exact hop where a network issue occurs.
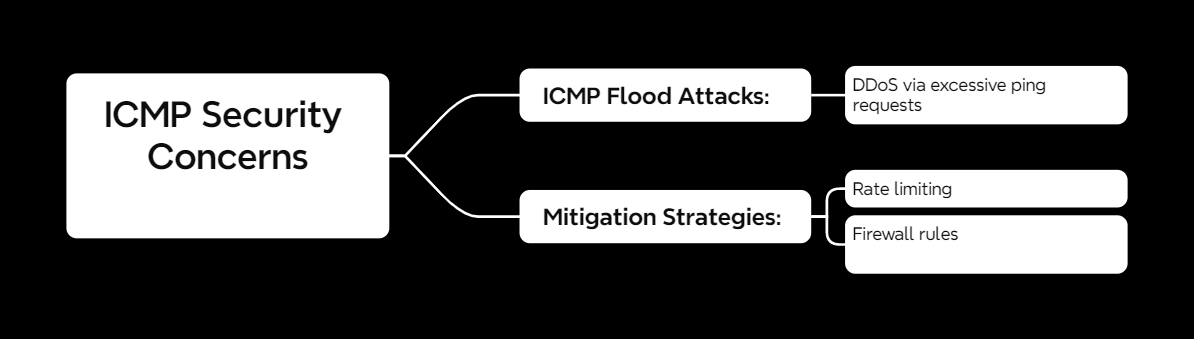
ICMP Security Concerns
ICMP is useful, but it can also be exploited:
⚠️ ICMP Flood Attacks: Sending excessive pings to overload a system (DDoS attack).
⚠️ Ping of Death: Sending oversized ICMP packets to crash a device.
🔒 Mitigating ICMP Attacks
- Rate limiting: Prevents excessive ICMP requests.
- Firewall rules: Blocks unnecessary ICMP traffic.